List of the Most Secure Internet Browsers in 2022

The browser is perhaps one of the most popular programs among all users, regardless of age, profession, social status. Since the introduction of the first browser, many programs of this kind have been designed. The number of only the most popular browsers is measured in dozens.
Experience shows that it is easier to win the heart of the user, giving them the most comfortable working conditions. Users also like the high speed of page loading. In most cases, the browser is selected based on these criteria. And someone takes advantage of the browser that is already available on the device or installs the most popular solution. It is difficult to call this choice conscious because not all browsers are equally safe.
It is advisable to use a reliable antivirus solution while working at home or for business purposes to ensure the additional level of security - read our business antivirus review to know why it is so important.
But if to speak about browsers, the market has some of the most secure options for you in 2022.
What is the Most Secure Browser?
Here is our list of the browsers we will review in terms of the security level:
- Mozilla Firefox
- Chromium Web Browser
- Brave Browser
- Opera
- Safari Browser
- Epic Browser
- Tor
1. Mozilla Firefox
- High load speed
- Frequent updates and robust protection against cyber-attacks
- A huge selection of extensions and additions
- Convenient tab system and tab manager
- Not suitable for the inexperienced users
- Has conflicts with Flash
- Cumbersome (the more add-ons you install on it, the slower it works)
Firefox is one of the best and most popular browsers in the world, still, some users wants to know the answer on the question “does Firefox track you”? Firefox is convenient, stable in operation, and also includes many features. At the same time, Firefox’s main advantages and disadvantages are plugins and add-ons. Even if you don’t install add-ons, Firefox will still be a safe and fast browser. Mozilla Firefox is very reliable and will rarely surprise you with mistakes and failures. As a rule, all bugs and errors are eliminated by regular updates.
Mozilla Firefox is almost the most advanced browser in terms of add-ons and extensions. Google Chrome may actually have a wider list of extensions, but Mozilla Firefox additions are much more functional.
The main difference between Mozilla Firefox additions is that most of them are created with applied purposes. By adding a specific set of extensions to your browser, you can change the functionality of the program in a few minutes.
- Turn the browser into an e-commerce office.
- Equip the web analyst and optimizer lab.
- Assemble a set of tools for research and training.
The new Mozilla Firefox browser has a built-in module for virus and phishing protection. All downloads from the Internet are automatically scanned for malicious threats. In addition, the password manager now has a master password, and you can safely use saved passcards directly in the browser without using third-party programs. Frequent updates provide an additional layer of Mozilla Firefox protection. This results in increased Internet traffic consumption. But security is above all else.
Mozilla Firefox easily deals with many simultaneously open tabs without much slowing down. Sometimes such an approach is very justified, for example, when you do voluminous work and use several sources of information from the Internet.
Overall, Firefox will be useful for everyone except beginners. A lot of innovations, convenience, security, and stable work - these are the three whales on which Firefox stays.
Perfect for: Windows, macOS, Linux.
Official site: https://www.mozilla.org/en-US/firefox/new/
2. Chromium Web Browser
- Highly-customizable browser
- Intuitive and easy-to-use
- Rather speedy, works smoothly
- Based on the open-source code
- Can be used for creating Chromium viruses
- Not secure enough
We have to thank Google for creating Chromium, an open-source web browser. According to developers, it provides users with fast, safe, and reliable Internet access. Dozens of browsers were created based on Chromium and Google Chrome as well.
The Chromium web browser can be used securely, but it has some shortcomings. Like many other open-source projects, it can be used for harmful purposes. Therefore, it is important to learn how to identify legitimate and potentially dangerous web browsers. Security experts have already noticed a new trend - the emergence of malicious Chromium browsers, such as the Chromium virus. Please, remember the following malicious browsers: Chroomium, Chedot, eFast, IQA Browser, Chromodo, Olcinium Browser, Securor, Torch.
Each of these programs can endanger your privacy and security. In addition, they can initiate unwanted changes to the system, cause web browsing failures, and other problems. Thus, the removal of Chromium browsers is strongly recommended. Fortunately, these fake tools can be deleted manually or automatically.
According to developers, speed, safety, and reliability are the primary categories that Chromium implies. In terms of functionality, it is very similar to Google Chrome, yet, you may notice several differences:
- Default Adobe Flash is not included.
- Open only free and standard video and audio formats.
- Automatic system updates are not applicable.
- Does not send error reports and statistics.
Chromium is not promoted as a full and independent browser, so you will not find the buttons for downloading the latest versions. The source code, discussion, and similar things for developers will be there. Still, you can find and download the latest version of Chromium in the form or archive.
No doubts, Chromium has many positive sides: it is fast, configurable, and lightweight. But is not perfect in terms of security, and Firefox is definitely a leader in the security competition between Chromium and Mozilla.
Perfect for: Windows, macOS, Linux.
Official site: https://www.chromium.org/Home
3. Brave Browser
- New Anonize technology
- Loads each site as part of a separate process
- Integration with Tor for better security
- Convenient visual statistics of blocked threats
- Open-source code allows creating viruses
- Increases its size while operating
Brave browser is a relatively new, but an up-and-coming browser solution. Brave is an open-source product based on Chromium. Its distinctive feature, which is visible even with minimal experience of use, is its effects visualization at the moment of the safety techniques usage.
On the main page of the Brave browser, you can see the visual statistics that include blocked trackers, advertising modules, saved time and traffic, and redirects from HTTP to HTTPS.
You can also view similar statistics for each web page by clicking on the lion button in the upper right corner. In the same window, you can quickly manage various security mechanisms built into the browser (so-called “shields”) for the current website: ad blocking parameters and cookies, browser fingerprint protection.
Brave also implemented interesting tabbing mechanisms:
- on behalf of “new personalities” from the set;
- “private”;
- “private” using Tor.
Tabs with a “new personality” emulate the download of the site by a completely new user. It creates a separate set of cookies and internal parameters for such a tab, which is not available for other open tabs. The use of such a mechanism allows, for example, to work conveniently with several accounts on social networks or mail, and generally prevents websites from providing information about various types of user activities. “Private” tabs differ in that they do not maintain a history of visiting pages, and cookies are cleared when the browser closes. “Private” tabs with Tor allow information to be transmitted through the Tor network.
The experimental function of improving safety by loading each site as part of a separate process gets our particular interest. Besides, the Anonize technology with the cryptographic zero-disclosure method increases the security level of the Brave browser.
Perfect for: Windows, macOS, Linux, Android, iOS
Official site: https://brave.com/features/
4. Opera
- Straightforward and understandable interface
- Has ad-block and VPN built-in features
- Includes Opera Turbo property
- Checks encrypted connections
- Lower security level than its competitors have
- Provides some ads and bookmarks
The inclusion of the Opera browser in this overview may seem to be a non-obvious step. Indeed, its capabilities are generally well known, and it is not positioned in the browser market as a security-focused solution. The vast number of security settings look familiar. However, Opera still stands out from many “traditional” browsers thanks to the built-in ad blocking mechanism, and most importantly, the presence of VPN. These features deserve separate consideration and, in many ways, allow Opera to withstand competition from numerous Chromium-based browsers.
Once the VPN is enabled, site handling is made from a virtual location. To change the virtual location, you can select the desired country from the list. If you select an inappropriate virtual location, the optimal location is automatically assigned. Once the VPN is enabled, the “bypass VPN in search engines” flag becomes available. The use of such a protective mechanism is much easier than in the Tor Browser, but the level of security is lower.
The presence of built-in tools to remove advertising blocks and prevent tracking user activity is also quite a pleasant surprise. On sites where you don’t want to block ads, you can turn off the blocker in 2 clicks. However, it is worth noting that as a kind of compensation for the care shown to protect the user from redundant information after installation in the browser already contains some volume of advertising in the form of bookmarks on various popular resources.
Opera supports private mode: when closing private windows, Opera deletes related data, including the history of visits, elements in the cache, cookies. In addition, Opera warns about suspicious pages by checking known phishing and malicious sites requested by the database. Finally, when browsing over an encrypted connection (https://), Opera checks to see if all parts of the site are encrypted. If you find that an active item on a page, such as a script, plugin, or frame, is served over an open connection (http://), all unsafe content is blocked. Of course, the page may not display correctly.
Perfect for: Windows, macOS, Linux, Android
Official site: https://www.opera.com/
5. Safari Browser
- Wide range of security tools
- Intelligent tracking system
- Secure sandbox to prevent malware infection
- Cross-Site scripting feature
- Not very fast while loading pages
- Complicated interface
Compared to previously mentioned search tools, Safari has more security flaws and errors that can be exploited by cybercriminals. However, Safari includes useful privacy and security measures to protect users from cyber threats:
- An intelligent tracking system that identifies advertisers and prevents tracking across sites.
- A built-in sandbox for a website that helps detect malicious codes and prevent malware penetration.
- A malicious site warning that appears before visiting a potentially dangerous or infected website.
- A private view feature that prevents your information from being collected and saved.
- A wide range of security and privacy settings to help disable location settings, enable the “don’t track” feature, and more.
Speaking about security, Apple primarily focuses on the Protected View feature. In this mode, Safari does not record the history of visited sites, downloaded software and documents, does not save search queries, cookies, and other data. Safari also includes pop-up blocking features.
To counteract attacks, Safari uses inter-site scripting (XSS - Cross-Site Scripting) that continues to develop. Also, the browser applies the reputational technologies to block malicious phishing and fraudulent sites. Safari browser includes support for EV certificates (Extended Validation), making it easy to highlight legitimate sites.

This browser is also marked with secure encryption technologies to prevent session interception and online fraud. Registration-based authentication on secure websites and the most popular proxy protocols are also supported. The Safe Downloads feature is also interesting: it displays the source from which every page was taken the first time you open each site.
Perfect for: macOS, iOS
Official site: https://www.apple.com/safari/
6. Epic Browser
- No Google products at all
- Instant deletion of cookies and trackers
- Includes encrypted proxy server
- Uses SSL connection
- Add-ons are not allowed
- Low download speed
Hidden Reflex’s Epic Privacy Browser is based on the open-source project Chromium - just like Google Chrome. However, the main difference is that Epic disables and removes all Google services. Therefore, the search giant cannot track the users’ activity (unless they enter Gmail and begin searching the Internet).
The main reason for including Epic in the list of secure browsers is that it only works in private view mode, and the anti-tracking feature is enabled by default. After each browsing session, Epic deletes cookies, trackers, and search-related data. In addition, the browser allows you to enable an encrypted proxy server that can protect you from disclosing IP address and other information from any Internet user.
If possible, Epic uses SSL connections, protects public Wi-Fi connections, and includes anti-advertising feature. Besides, the program does not collect any information about users. The only information Epic is interested in is an IP address to obtain search results of geographical significance.
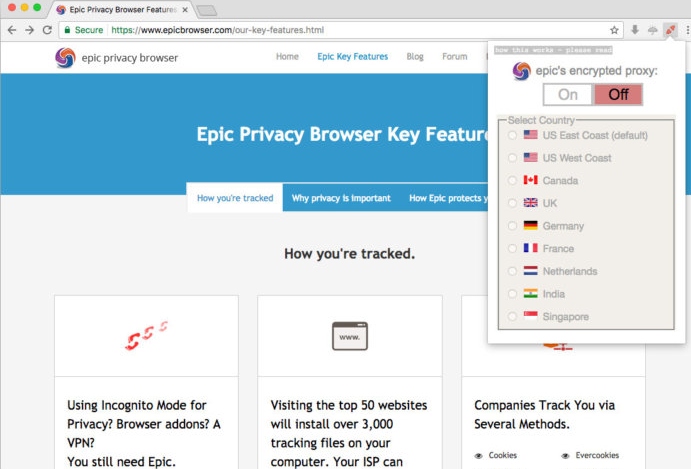
However, one of the main disadvantages is that this browser does not allow the installation of add-ons. The company argues that extensions are one of the most dangerous components that put a user’s privacy at risk. Therefore, they only support a few add-ons that can be trusted. It also reports when the website was loaded or when standard search modifiers were skipped.
Perfect for: Windows, macOS
Official site: https://www.epicbrowser.com/
7. Tor
- Guarantees high level of anonymity
- Hides the real IP address
- Clears all the activity-related information
- Utilizes multiple level of encryption
- Sluggish performance and speed
- Complicated for newbies
If we speak about the secure browser, we can’t help but mention Tor. The browser itself appeared in 2008, although the development of the system began in 1995. The system has a free license and the ope-source code. The idea of the Tor browser is to give the user real freedom and anonymity.
The principle of the Tor operation is as follows: before the data gets through the output server, it passes through three nodes. Data between nodes is encrypted, and only the nodes know the keys to the ciphers. As a result, at the output, the user does not leave any traces of visit on the site. It is important to understand that Tor is a traffic anonymizer, not the encryptor. To stay secure, it is desirable to use VPN in addition to Tor, as well as to use HTTPS whenever possible.
It is also worth remembering that the speed of information transmission leaves much to be desired. The user’s IP is encrypted by passing through many proxy servers located around the world that reduce page loading speed.
The entire Tor project is managed by volunteers and is designed for network users to browse web pages anonymously. The program hides the IP address, location, activiry-related information, and uses multiple levels of encryption to prevent anyone from seeing your actions online. However, this is not a VPN service.
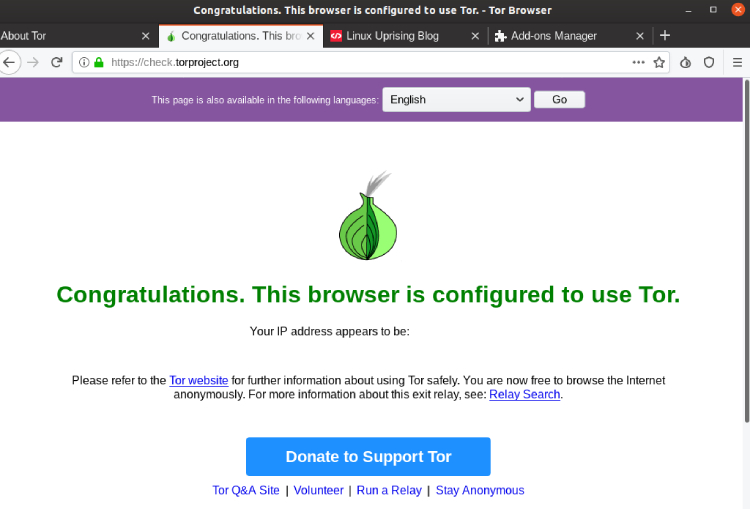
Among the disadvantages of Tor are sluggish performance, uncomfortable and slightly complicated use. In addition, government agencies can still see you are using Tor. Even though they can’t see which sites you use and what actions you perform, you may be considered suspicious.
Perfect for: Windows, Linux, macOS
Official site: https://www.torproject.org/
Bottom Line
There is no absolutely secure browser, as there is no absolute security in principle. Each of the presented solutions has known pros and cons, and has its admirers and critics. This is natural, as the goals, expectations, way of life of people differ, and, accordingly, the level of necessary protection is not a constant value either. If to speak about our personal preference, we highlight Mozilla Firefox due to the range of its security features, compatibility with various platforms, and frequent updates.
Overall, the main conclusion is that the selection criteria set of the appropriate browser need to be extended, taking into account the risks of privacy violation. At the same time, it should be understood that increased security can often involve loss in convenience and speed of Internet operation. Functions of auto-fill logins and passwords, synchronization of user data with external servers, maintenance of the history of visits make life easier but affect security level negatively.



Comments